Bluff (poker): Difference between revisions
No edit summary |
No edit summary |
||
| Line 1: | Line 1: | ||
[[File:Vigenere.jpg|right|thumbnail|The Vigenère cipher is named for Blaise de Vigenère (pictured). Although [[Giovan Battista Bellaso]] had invented the cipher earlier, Vigenère did invent a stronger [[autokey cipher]].]] | |||
[[File:Confederate cipher disk.png|right|thumb|A reproduction of the Confederacy's cipher disk on display at the [[National Cryptologic Museum]]]] | |||
The '''Vigenère cipher''' is a method of [[encryption|encrypting]] [[alphabet]]ic text by using a series of different [[Caesar cipher]]s based on the letters of a keyword. It is a simple form of [[Polyalphabetic cipher|polyalphabetic substitution]].<ref>{{cite book|authors=Bruen, Aiden A. & Forcinito, Mario A.|title=Cryptography, Information Theory, and Error-Correction: A Handbook for the 21st Century|publisher=John Wiley & Sons|year=2011|isbn=978-1-118-03138-4|page=21|url=http://books.google.com/books?id=fd2LtVgFzoMC&pg=PA21}}</ref><ref>{{cite book|author=Martin, Keith M.|title=Everyday Cryptography|publisher=Oxford University Press|year=2012|isbn=978-0-19-162588-6|page=142|url=http://books.google.com/books?id=1NHli2uzt_EC&pg=PT142}}</ref> | |||
The Vigenère ({{IPA-fr|viʒnɛːʁ}}) cipher has been reinvented many times. The method was originally described by [[Giovan Battista Bellaso]] in his 1553 book ''La cifra del. Sig. Giovan Battista Bellaso''; however, the scheme was later misattributed to [[Blaise de Vigenère]] in the 19th century, and is now widely known as the "Vigenère cipher".{{Citation needed|date=April 2012}} | |||
Though the cipher is easy to understand and implement, for three centuries it resisted all attempts to break it; this earned it the description '''le chiffre indéchiffrable''' (French for 'the indecipherable cipher'). Many people have tried to implement encryption schemes that are essentially Vigenère ciphers.<ref>{{cite book|first=Laurence D.|last=Smith|year=1943|title=Cryptography the Science of Secret Writing: The Science of Secret Writing|chapter=Substitution Ciphers|editor=|others=|pages=81|publisher=Dover Publications|isbn=0-486-20247-X}}</ref> [[ Friedrich Kasiski]] was the first to publish a general method of deciphering a Vigenère cipher. | |||
==History== | |||
The first well documented description of a polyalphabetic cipher was formulated by [[Leon Battista Alberti]] around 1467 and used a metal cipher disc to switch between cipher alphabets. Alberti's system only switched alphabets after several words, and switches were indicated by writing the letter of the corresponding alphabet in the ciphertext. Later, in 1508, [[Johannes Trithemius]], in his work ''Poligraphia'', invented the [[tabula recta]], a critical component of the Vigenère cipher. The [[Trithemius cipher]], however, only provided a progressive, rigid and predictable system for switching between cipher alphabets.{{Citation needed|date=April 2012}} | |||
What is now known as the Vigenère cipher was originally described by [[Giovan Battista Bellaso]] in his 1553 book ''La cifra del. Sig. Giovan Battista Bellaso''. He built upon the tabula recta of Trithemius, but added a repeating "countersign" (a [[Key (cryptography)|key]]) to switch cipher alphabets every letter. Whereas Alberti and Trithemius used a fixed pattern of substitutions, Bellaso's scheme meant the pattern of substitutions could be easily changed simply by selecting a new key. Keys were typically single words or short phrases, known to both parties in advance, or transmitted "out of band" along with the message. Bellaso's method thus required strong security for only the key. As it is relatively easy to secure a short key phrase, say by a previous private conversation, Bellaso's system was considerably more secure.{{Citation needed|date=April 2012}} | |||
[[Blaise de Vigenère]] published his description of a similar but stronger [[autokey cipher]] before the court of [[Henry III of France]], in 1586. Later, in the 19th century, the invention of Bellaso's cipher was misattributed to Vigenère. David Kahn in his book ''The Codebreakers'' lamented the misattribution by saying that history had "ignored this important contribution and instead named a regressive and elementary cipher for him [Vigenère] though he had nothing to do with it".<ref name="KahnOrigin">{{cite book|first=Kahn|last=David|year=1999|title=The Codebreakers: The Story of Secret Writing|chapter=On the Origin of a Species|publisher=Simon & Schuster|isbn=0-684-83130-9}}</ref> | |||
The Vigenère cipher gained a reputation for being exceptionally strong. Noted author and mathematician Charles Lutwidge Dodgson ([[Lewis Carroll]]) called the Vigenère cipher unbreakable in his 1868 piece "[[The Alphabet Cipher]]" in a children's magazine. In 1917, ''[[Scientific American]]'' described the Vigenère cipher as "impossible of translation".<ref>{{cite book|first=Lars R.|last=Knudsen|year=1998|title=State of the Art in Applied Cryptography: Course on Computer Security and Industrial Cryptograph Leuven Belgium, June 1997 Revised Lectures |chapter=Block Ciphers— a survey|editor=Bart Preneel and Vincent Rijmen|others=|pages=29|publisher=Springer|isbn=3-540-65474-7|location=Berlin ; London}}</ref> This reputation was not deserved. [[Charles Babbage]] is known to have broken a variant of the cipher as early as 1854; however, he didn't publish his work.<ref name="Singh">{{cite book|first=Simon|last=Singh|year=1999|title=The Code Book|chapter=Chapter 2: Le Chiffre Indéchiffrable|editor=|pages=63–78|publisher=[[Anchor Books#Divisions and imprints|Anchor Books]], [[Random House]]|isbn=0-385-49532-3}}</ref> Kasiski entirely broke the cipher and published the technique in the 19th century. Even before this, though, some skilled cryptanalysts could occasionally break the cipher in the 16th century.<ref name="KahnOrigin" /> | |||
[[File:Cryptographic sliding rule-IMG 0533.jpg|thumb|Cryptographic slide rule used as a calculation aid by the Swiss Army between 1914 and 1940.]] | |||
The Vigenère cipher is simple enough to be a field cipher if it is used in conjunction with cipher disks.<ref>[http://www.vectorsite.net/ttcode_03.html#m2 Codes, Ciphers, & Codebreaking] (The Rise Of Field Ciphers)</ref> The [[Confederate States of America]], for example, used a brass cipher disk to implement the Vigenère cipher during the [[American Civil War]]. The Confederacy's messages were far from secret and the Union regularly cracked their messages. Throughout the war, the Confederate leadership primarily relied upon three key phrases, "Manchester Bluff", "Complete Victory" and, as the war came to a close, "Come Retribution".<ref>{{cite book|first=Kahn|last=David|year=1999|title=The Codebreakers: The Story of Secret Writing|chapter=Crises of the Union|pages=217–221|publisher=Simon & Schuster|isbn=0-684-83130-9}}</ref> | |||
[[Gilbert Vernam]] tried to repair the broken cipher (creating the Vernam-Vigenère cipher in 1918), but, no matter what he did, the cipher was still vulnerable to cryptanalysis. Vernam's work, however, eventually led to the [[one-time pad]], a provably unbreakable cipher.{{Citation needed|date=April 2012}} | |||
==Description== | |||
[[File:Vigenère square shading.svg|thumb|The Vigenère square or Vigenère table, also known as the ''[[tabula recta]]'', can be used for encryption and decryption.]] | |||
In a [[Caesar cipher]], each letter of the alphabet is shifted along some number of places; for example, in a Caesar cipher of shift 3, <tt>A</tt> would become <tt>D</tt>, <tt>B</tt> would become <tt>E</tt>, <tt>Y</tt> would become <tt>B</tt> and so on. The Vigenère cipher consists of several Caesar ciphers in sequence with different shift values. | |||
To encrypt, a table of alphabets can be used, termed a ''[[tabula recta]]'', ''Vigenère square'', or ''Vigenère table''. It consists of the alphabet written out 26 times in different rows, each alphabet shifted cyclically to the left compared to the previous alphabet, corresponding to the 26 possible Caesar ciphers. At different points in the encryption process, the cipher uses a different alphabet from one of the rows. The alphabet used at each point depends on a repeating keyword.{{Citation needed|date=April 2012}} | |||
For example, suppose that the [[plaintext]] to be encrypted is: | |||
:<tt>ATTACKATDAWN</tt> | |||
The person sending the message chooses a keyword and repeats it until it matches the length of the plaintext, for example, the keyword "LEMON": | |||
:<tt>LEMONLEMONLE</tt> | |||
Each row starts with a key letter. The remainder of the row holds the letters A to Z (in shifted order). Although there are 26 key rows shown, you will only use as many keys (different alphabets) as there are unique letters in the key string, here just 5 keys, {L, E, M, O, N}. For successive letters of the message, we are going to take successive letters of the key string, and encipher each message letter using its corresponding key row. Choose the next letter of the key, go along that row to find the column heading that matches the message character; the letter at the intersection of [key-row, msg-col] is the enciphered letter. | |||
For example, the first letter of the plaintext, <tt>A</tt>, is paired with <tt>L</tt>, the first letter of the key. So use row <tt>L</tt> and column <tt>A</tt> of the Vigenère square, namely <tt>L</tt>. Similarly, for the second letter of the plaintext, the second letter of the key is used; the letter at row <tt>E</tt> and column <tt>T</tt> is <tt>X</tt>. The rest of the plaintext is enciphered in a similar fashion: | |||
{| | |||
| Plaintext: || <tt>ATTACKATDAWN</tt> | |||
|- | |||
| Key: || <tt>LEMONLEMONLE</tt> | |||
|- | |||
| Ciphertext: || <tt>LXFOPVEFRNHR</tt> | |||
|} | |||
Decryption is performed by going to the row in the table corresponding to the key, finding the position of the ciphertext letter in this row, and then using the column's label as the plaintext. For example, in row <tt>L</tt> (from ''L''EMON), the ciphertext <tt>L</tt> appears in column <tt>A</tt>, which is the first plaintext letter. Next we go to row <tt>E</tt> (from L''E''MON), locate the ciphertext <tt>X</tt> which is found in column <tt>T</tt>, thus <tt>T</tt> is the second plaintext letter. | |||
==Algebraic description== | |||
Vigenère can also be viewed algebraically. If the letters <tt>A</tt>–<tt>Z</tt> are taken to be the numbers 0–25, and addition is performed [[modular arithmetic|modulo]] 26, then Vigenère encryption <math>E</math> using the key <math>K</math> can be written, | |||
:<math>C_i = E_K(M_i) = (M_i+K_i) \mod {26}</math> | |||
and decryption <math>D</math> using the key <math>K</math>, | |||
:<math>M_i = D_K(C_i) = (C_i-K_i) \mod {26}</math>, | |||
whereas <math>M = M_0 \dots M_n</math> is the message, <math>C = C_0 \dots C_n</math> is the ciphertext and <math>K = K_0 \dots K_m</math> is the used key. | |||
Thus using the previous example, to encrypt <math>A \widehat{=} 0</math> with key letter <math>L \widehat{=} 11</math> the calculation would result in <math>11 \widehat{=} L</math>. | |||
:<math>11 = (0+11) \mod {26}</math> | |||
Therefore to decrypt <math>R \widehat{=} 17</math> with key letter <math>E \widehat{=} 4</math> the calculation would result in <math>13 \widehat{=} N</math>. | |||
:<math>13 = (17-4) \mod {26}</math> | |||
==Cryptanalysis== | |||
[[File:Vigenere letter frequencies.PNG|thumb|The Vigenère cipher masks the characteristic letter frequencies of English plaintexts, but some patterns remain.]] | |||
The idea behind the Vigenère cipher, like all polyalphabetic ciphers, is to disguise plaintext [[letter frequencies]], which interferes with a straightforward application of [[frequency analysis]]. For instance, if <tt>P</tt> is the most frequent letter in a ciphertext whose plaintext is in [[English language|English]], one might suspect that <tt>P</tt> corresponds to <tt>E</tt>, because <tt>E</tt> is the most frequently used letter in English. However, using the Vigenère cipher, <tt>E</tt> can be enciphered as different ciphertext letters at different points in the message, thus defeating simple frequency analysis. | |||
The primary weakness of the Vigenère cipher is the repeating nature of its [[Key (cryptography)|key]]. If a cryptanalyst correctly guesses the key's length, then the cipher text can be treated as interwoven [[Caesar cipher]]s, which individually are easily broken. The Kasiski and Friedman tests can help determine the key length. | |||
===Kasiski examination=== | |||
:''For more details on this topic, see [[Kasiski examination]].''<!-- details --> | |||
In 1863 [[Friedrich Kasiski]] was the first to publish a successful general attack on the Vigenère cipher. Earlier attacks relied on knowledge of the plaintext, or use of a recognizable word as a key. Kasiski's method had no such dependencies. Kasiski was the first to publish an account of the attack, but it is clear that there were others who were aware of it. In 1854, [[Charles Babbage]] was goaded into breaking the Vigenère cipher when John Hall Brock Thwaites submitted a "new" cipher to the Journal of the Society of the Arts. When Babbage showed that Thwaites' cipher was essentially just another recreation of the Vigenère cipher, Thwaites challenged Babbage to break his cipher encoded twice, with keys of different length. Babbage succeeded in decrypting a sample, which turned out to be the poem "The Vision of Sin", by [[Alfred Tennyson]], encrypted according to the keyword "Emily", the first name of Tennyson's wife. Babbage never explained the method he used. Studies of Babbage's notes reveal that he had used the method later published by Kasiski, and suggest that he had been using the method as early as 1846.<ref>Franksen, O. I. (1985) Mr. Babbage's Secret: The Tale of a Cipher—and APL. Prentice Hall.</ref> | |||
The [[Kasiski examination]], also called the Kasiski test, takes advantage of the fact that repeated words may, by chance, sometimes be encrypted using the same key letters, leading to repeated groups in the ciphertext. For example, Consider the following encryption using the keyword <tt>ABCD</tt>: | |||
Key: ABCDABCDABCDABCDABCDABCDABCD | |||
Plaintext: '''''CRYPTO'''''ISSHORTFOR'''''CRYPTO'''''GRAPHY | |||
Ciphertext: '''''CSASTP'''''KVSIQUTGQU'''''CSASTP'''''IUAQJB | |||
There is an easily seen repetition in the ciphertext, and the Kasiski test will be effective. | |||
Here the distance between the repetitions of <tt>CSASTP</tt> is 16. Assuming that the repeated segments represent the same plaintext segments, this implies that the key is 16, 8, 4, 2, or 1 characters long. (All [[Factorization|factors]] of the distance are possible key lengths – a key of length one is just a simple [[caesar cipher]], where cryptanalysis is much easier.) Since key lengths 2 and 1 are unrealistically short, one only needs to try lengths 16, 8, or 4. Longer messages make the test more accurate because they usually contain more repeated ciphertext segments. The following ciphertext has two segments that are repeated: | |||
Ciphertext: '''''VHVS'''''SP'''''QUCE'''''MRVBVBBB'''''VHVS'''''URQGIBDUGRNICJ'''''QUCE'''''RVUAXSSR | |||
The distance between the repetitions of <tt>VHVS</tt> is 18. Assuming that the repeated segments represent the same plaintext segments, this implies that the key is 18, 9, 6, 3, 2, or 1 characters long. The distance between the repetitions of <tt>QUCE</tt> is 30 characters. This means that the key length could be 30, 15, 10, 6, 5, 3, 2, or 1 characters long. By taking the [[Intersection (set theory)|intersection]] of these sets one could safely conclude that the most likely key length is 6, since 3, 2, and 1 are unrealistically short.<!-- the key is CARBON and the message is THERECOULDYETBEANOTHERGEOGRAPHERWHOWOULDDISAGREE --> | |||
===Friedman test=== | |||
The Friedman test (sometimes known as the kappa test) was invented during the 1920s by [[William F. Friedman]]. Friedman used the [[index of coincidence]], which measures the unevenness of the cipher letter frequencies to break the cipher. By knowing the probability <math>\kappa_p</math> that any two randomly chosen source-language letters are the same (around 0.067 for monocase English) and the probability of a coincidence for a uniform random selection from the alphabet <math>\kappa_r</math> (1/26 = 0.0385 for English), the key length can be estimated as: | |||
: <math>{\kappa_p-\kappa_r}\over{\kappa_o-\kappa_r}</math> | |||
from the observed coincidence rate | |||
: <math>\kappa_o=\frac{\sum_{i=1}^{c}n_i(n_i -1)}{N(N-1)}</math> | |||
where ''c'' is the size of the alphabet (26 for English), ''N'' is the length of the text, and ''n''<sub>1</sub> through ''n''<sub>''c''</sub> are the observed ciphertext [[letter frequencies]], as integers. | |||
This is, however, only an approximation whose accuracy increases with the size of the text. It would in practice be necessary to try various key lengths close to the estimate.<ref>{{cite book |editor=Henk C.A. van Tilborg |title=Encyclopedia of Cryptography and Security |publisher=Springer |edition=First |isbn=0-387-23473-X |pages=115 |year=2005}}</ref> A better approach for repeating-key ciphers is to copy the ciphertext into rows of a matrix having as many columns as an assumed key length, then compute the average [[Index of coincidence#Example|index of coincidence]] with each column considered separately; when this is done for each possible key length, the highest average I.C. then corresponds to the most likely key length.<ref>{{cite journal | author=Mountjoy, Marjorie | title= The Bar Statistics | journal=NSA Technical Journal | year=1963 | volume=VII | issue=2,4}} Published in two parts.</ref> Such tests may be supplemented by information from the Kasiski examination. | |||
===Frequency analysis=== | |||
Once the length of the key is known, the ciphertext can be rewritten into that many columns, with each column corresponding to a single letter of the key. Each column consists of plaintext that has been encrypted by a single [[Caesar cipher]]; the Caesar key (shift) is just the letter of the Vigenère key that was used for that column. Using methods similar to those used to break the Caesar cipher, the letters in the ciphertext can be discovered. | |||
An improvement to the Kasiski examination, known as [[Auguste Kerckhoffs|Kerckhoffs]]' method, matches each column's letter frequencies to shifted plaintext frequencies to discover the key letter (Caesar shift) for that column. Once every letter in the key is known, the cryptanalyst can simply decrypt the ciphertext and reveal the plaintext.<ref>{{cite web |url=http://courses.umass.edu/cs415/labs/lab1/415-lab1-crypto.pdf |title=Lab exercise: Vigenere, RSA, DES, and Authentication Protocols |accessdate=2006-11-10 |format=PDF |work=CS 415: Computer and Network Security }}</ref> Kerckhoffs' method is not applicable when the Vigenère table has been scrambled, rather than using normal alphabetic sequences, although Kasiski examination and coincidence tests can still be used to determine key length in that case. | |||
===Key elimination=== | |||
The Vigenère cipher function is essentially modulo arithmetic, and thus commutative. So if the key length is known (or guessed) then subtracting the cipher text from itself, offset by the key length will produce the cipher text encrypted with itself. If any words in the cipher text are known or can be guessed, then the plain text and also the key, will be revealed. This is useful if the key is an obscure sequence of letters because the plain text will generally be ordinary words. | |||
Key elimination is useful for making short versions of the plain text. | |||
==Variants== | |||
[[File:Confederate cipher wheel (Vigenere), captured at the surrender of Mobile, Alabama, in May 1865 - National Cryptologic Museum - DSC07710.JPG|thumb|left|Confederate cipher wheel, captured at the surrender of [[Mobile, Alabama]], in May 1865 - [[National Cryptologic Museum]]]] | |||
The [[running key cipher|running key]] variant of the Vigenère cipher was also considered unbreakable at one time. This version uses as the key a block of text as long as the plaintext. Since the key is as long as the message the Friedman and Kasiski tests no longer work (the key is not repeated). In 1920, Friedman was the first to discover this variant's weaknesses. The problem with the running key Vigenère cipher is that the cryptanalyst has statistical information about the key (assuming that the block of text is in a known language) and that information will be reflected in the ciphertext. | |||
If using a key which is truly random, is at least as long as the encrypted message and is used only once, the Vigenère cipher is theoretically unbreakable. However, in this case it is the key, not the cipher, which provides cryptographic strength and such systems are properly referred to collectively as [[one-time pad]] systems, irrespective of which ciphers are employed. | |||
Vigenère actually invented a stronger cipher: an [[autokey cipher]]. The name "Vigenère cipher" became associated with a simpler polyalphabetic cipher instead. In fact, the two ciphers were often confused, and both were sometimes called "''le chiffre indéchiffrable''". Babbage actually broke the much stronger autokey cipher, while Kasiski is generally credited with the first published solution to the fixed-key polyalphabetic ciphers. | |||
A simple variant is to encrypt using the Vigenère decryption method, and decrypt using Vigenère encryption. This method is sometimes referred to as "Variant Beaufort". This is different from the [[Beaufort cipher]], created by Sir [[Francis Beaufort]], which nonetheless is similar to Vigenère but uses a slightly modified enciphering mechanism and tableau. The Beaufort cipher is a [[reciprocal cipher]]. | |||
Despite the Vigenère cipher's apparent strength it never became widely used throughout Europe. The [[Gronsveld|Gronsfeld]] cipher is a variant created by Count Gronsfeld which is identical to the Vigenère cipher, except that it uses just 10 different cipher alphabets (corresponding to the digits 0 to 9). The Gronsfeld cipher is strengthened because its key is not a word, but it is weakened because it has just 10 cipher alphabets. Gronsfeld's cipher did become widely used throughout Germany and Europe, despite its weaknesses. | |||
==See also== | |||
* [[Roger Frontenac]] ([[Nostradamus]] quatrain decryptor, 1950) | |||
==References== | |||
{{reflist|2}} | |||
==Sources== | |||
* {{cite book|first=Albrecht|last=Beutelspacher|year=1994|title=Cryptology|chapter=Chapter 2|editor=|others=translation from German by J. Chris Fisher|pages=27–41|publisher=Mathematical Association of America|isbn=0-883-85504-6|location=Washington, DC}} | |||
* {{cite book|first=Simon|last=Singh| authorlink=Simon Singh|year=1999|title=[[The Code Book]]|chapter=Chapter 2: Le Chiffre Indéchiffrable|editor=|pages=|publisher=Anchor Book, [[Random House]]|isbn=0-385-49532-3}} | |||
* {{cite book|first=Helen Fouche|last=Gaines|year=1939|title=Cryptanalysis a Study of Ciphers and Their Solutions|chapter=The Gronsfeld, Porta and Beaufort Ciphers|editor=|pages=117–126|publisher=[[Dover Publications]]|isbn=0-486-20097-3}} | |||
* {{cite journal |last=Mendelsohn |first=Charles J |year=1940 |title=Blaise De Vigenere and The 'Chiffre Carre' |journal=Proceedings of the American Philosophical Society |volume=82 |number=2}} | |||
==External links== | |||
===Articles=== | |||
* [http://home.att.net/~tleary/cryptolo.htm History of the cipher from Cryptologia] | |||
* [http://www.bbc.co.uk/dna/h2g2/alabaster/A613135 Basic Cryptanalysis] at H2G2 | |||
* [http://www.math.ucdenver.edu/~wcherowi/courses/m5410/m5410cc.html Lecture Notes on Classical Cryptology including an explanation and derivation of the Friedman Test] | |||
* [http://web.archive.org/web/20110624100854/http://www.aolnews.com/2010/12/25/civil-war-message-in-a-bottle-opened-decoded/ aolnews.com] | |||
===Programming=== | |||
* [http://inventwithpython.com/hacking ''Hacking Secret Ciphers with Python''] [http://inventwithpython.com/hacking/chapter19.html Chapter 19, The Vigenère Cipher], [http://inventwithpython.com/hacking/chapter21.html Chapter 21, Hacking the Vigenère Cipher], with Python source code. | |||
* [http://www.asecuritysite.com/security/Coding/vigcalc Online Vigenère Cipher] | |||
* [http://sharkysoft.com/misc/vigenere/ Sharky's Online Vigenere Cipher] — Encode and decode messages, using a known key, within a Web browser ([[JavaScript]]) | |||
* [http://smurfoncrack.com/pygenere/ PyGenere: an online tool for automatically deciphering Vigenère-encoded texts] (6 languages supported) | |||
* [http://ljplawcom00.web707.discountasp.net/Vigenere/Vigenere.aspx/ Vigenère Cipher encryption and decryption program (browser version, English only)] | |||
* [https://metacpan.org/module/Crypt::Vigenere Crypt::Vigenere] — a [[CPAN]] module implementing the Vigenère cipher | |||
* [http://www.perlmonks.org/?node_id=550450 Breaking the indecipherable cipher: Perl code to decipher Vigenère text, with the source in the shape of Babbage's head] | |||
* [http://papacharliefox3.wordpress.com/2009/04/02/desafio-de-crypto-ii-cifra-de-vigenere/ Vigenère in BASH] | |||
* [http://www.vigenere.tk Java Vigenere] applet with source code ([[GNU General Public License|GNU GPL]]) | |||
* [http://log.flirt-wind.net/2010/08/vigenere-cipher-in-java/ Vigenere Cipher in Java] | |||
* [http://sourceforge.net/projects/tstools/ Vijner 974 Encryption Tool in C# (Vigenere Algorithm)] | |||
* [http://www.vigenere.net/ Vigenère Cipher encryption tool] - Browser | |||
* [https://chrome.google.com/webstore/detail/jefmgpafeddooefhpnhccodndbcpbmhj Vigenère Cipher encryption tool] - Google Chrome extension | |||
{{Cryptography navbox | classical}} | |||
{{DEFAULTSORT:Vigenere Cipher}} | |||
[[Category:Classical ciphers]] | |||
[[Category:Stream ciphers]] | |||
{{Link FA|hr}} | |||
Revision as of 19:32, 20 November 2013


The Vigenère cipher is a method of encrypting alphabetic text by using a series of different Caesar ciphers based on the letters of a keyword. It is a simple form of polyalphabetic substitution.[1][2]
The Vigenère (Template:IPA-fr) cipher has been reinvented many times. The method was originally described by Giovan Battista Bellaso in his 1553 book La cifra del. Sig. Giovan Battista Bellaso; however, the scheme was later misattributed to Blaise de Vigenère in the 19th century, and is now widely known as the "Vigenère cipher".Potter or Ceramic Artist Truman Bedell from Rexton, has interests which include ceramics, best property developers in singapore developers in singapore and scrabble. Was especially enthused after visiting Alejandro de Humboldt National Park.
Though the cipher is easy to understand and implement, for three centuries it resisted all attempts to break it; this earned it the description le chiffre indéchiffrable (French for 'the indecipherable cipher'). Many people have tried to implement encryption schemes that are essentially Vigenère ciphers.[3] Friedrich Kasiski was the first to publish a general method of deciphering a Vigenère cipher.
History
The first well documented description of a polyalphabetic cipher was formulated by Leon Battista Alberti around 1467 and used a metal cipher disc to switch between cipher alphabets. Alberti's system only switched alphabets after several words, and switches were indicated by writing the letter of the corresponding alphabet in the ciphertext. Later, in 1508, Johannes Trithemius, in his work Poligraphia, invented the tabula recta, a critical component of the Vigenère cipher. The Trithemius cipher, however, only provided a progressive, rigid and predictable system for switching between cipher alphabets.Potter or Ceramic Artist Truman Bedell from Rexton, has interests which include ceramics, best property developers in singapore developers in singapore and scrabble. Was especially enthused after visiting Alejandro de Humboldt National Park.
What is now known as the Vigenère cipher was originally described by Giovan Battista Bellaso in his 1553 book La cifra del. Sig. Giovan Battista Bellaso. He built upon the tabula recta of Trithemius, but added a repeating "countersign" (a key) to switch cipher alphabets every letter. Whereas Alberti and Trithemius used a fixed pattern of substitutions, Bellaso's scheme meant the pattern of substitutions could be easily changed simply by selecting a new key. Keys were typically single words or short phrases, known to both parties in advance, or transmitted "out of band" along with the message. Bellaso's method thus required strong security for only the key. As it is relatively easy to secure a short key phrase, say by a previous private conversation, Bellaso's system was considerably more secure.Potter or Ceramic Artist Truman Bedell from Rexton, has interests which include ceramics, best property developers in singapore developers in singapore and scrabble. Was especially enthused after visiting Alejandro de Humboldt National Park.
Blaise de Vigenère published his description of a similar but stronger autokey cipher before the court of Henry III of France, in 1586. Later, in the 19th century, the invention of Bellaso's cipher was misattributed to Vigenère. David Kahn in his book The Codebreakers lamented the misattribution by saying that history had "ignored this important contribution and instead named a regressive and elementary cipher for him [Vigenère] though he had nothing to do with it".[4]
The Vigenère cipher gained a reputation for being exceptionally strong. Noted author and mathematician Charles Lutwidge Dodgson (Lewis Carroll) called the Vigenère cipher unbreakable in his 1868 piece "The Alphabet Cipher" in a children's magazine. In 1917, Scientific American described the Vigenère cipher as "impossible of translation".[5] This reputation was not deserved. Charles Babbage is known to have broken a variant of the cipher as early as 1854; however, he didn't publish his work.[6] Kasiski entirely broke the cipher and published the technique in the 19th century. Even before this, though, some skilled cryptanalysts could occasionally break the cipher in the 16th century.[4]

The Vigenère cipher is simple enough to be a field cipher if it is used in conjunction with cipher disks.[7] The Confederate States of America, for example, used a brass cipher disk to implement the Vigenère cipher during the American Civil War. The Confederacy's messages were far from secret and the Union regularly cracked their messages. Throughout the war, the Confederate leadership primarily relied upon three key phrases, "Manchester Bluff", "Complete Victory" and, as the war came to a close, "Come Retribution".[8]
Gilbert Vernam tried to repair the broken cipher (creating the Vernam-Vigenère cipher in 1918), but, no matter what he did, the cipher was still vulnerable to cryptanalysis. Vernam's work, however, eventually led to the one-time pad, a provably unbreakable cipher.Potter or Ceramic Artist Truman Bedell from Rexton, has interests which include ceramics, best property developers in singapore developers in singapore and scrabble. Was especially enthused after visiting Alejandro de Humboldt National Park.
Description

In a Caesar cipher, each letter of the alphabet is shifted along some number of places; for example, in a Caesar cipher of shift 3, A would become D, B would become E, Y would become B and so on. The Vigenère cipher consists of several Caesar ciphers in sequence with different shift values.
To encrypt, a table of alphabets can be used, termed a tabula recta, Vigenère square, or Vigenère table. It consists of the alphabet written out 26 times in different rows, each alphabet shifted cyclically to the left compared to the previous alphabet, corresponding to the 26 possible Caesar ciphers. At different points in the encryption process, the cipher uses a different alphabet from one of the rows. The alphabet used at each point depends on a repeating keyword.Potter or Ceramic Artist Truman Bedell from Rexton, has interests which include ceramics, best property developers in singapore developers in singapore and scrabble. Was especially enthused after visiting Alejandro de Humboldt National Park.
For example, suppose that the plaintext to be encrypted is:
- ATTACKATDAWN
The person sending the message chooses a keyword and repeats it until it matches the length of the plaintext, for example, the keyword "LEMON":
- LEMONLEMONLE
Each row starts with a key letter. The remainder of the row holds the letters A to Z (in shifted order). Although there are 26 key rows shown, you will only use as many keys (different alphabets) as there are unique letters in the key string, here just 5 keys, {L, E, M, O, N}. For successive letters of the message, we are going to take successive letters of the key string, and encipher each message letter using its corresponding key row. Choose the next letter of the key, go along that row to find the column heading that matches the message character; the letter at the intersection of [key-row, msg-col] is the enciphered letter.
For example, the first letter of the plaintext, A, is paired with L, the first letter of the key. So use row L and column A of the Vigenère square, namely L. Similarly, for the second letter of the plaintext, the second letter of the key is used; the letter at row E and column T is X. The rest of the plaintext is enciphered in a similar fashion:
| Plaintext: | ATTACKATDAWN |
| Key: | LEMONLEMONLE |
| Ciphertext: | LXFOPVEFRNHR |
Decryption is performed by going to the row in the table corresponding to the key, finding the position of the ciphertext letter in this row, and then using the column's label as the plaintext. For example, in row L (from LEMON), the ciphertext L appears in column A, which is the first plaintext letter. Next we go to row E (from LEMON), locate the ciphertext X which is found in column T, thus T is the second plaintext letter.
Algebraic description
Vigenère can also be viewed algebraically. If the letters A–Z are taken to be the numbers 0–25, and addition is performed modulo 26, then Vigenère encryption using the key can be written,
and decryption using the key ,
whereas is the message, is the ciphertext and is the used key.
Thus using the previous example, to encrypt with key letter the calculation would result in .
Therefore to decrypt with key letter the calculation would result in .
Cryptanalysis
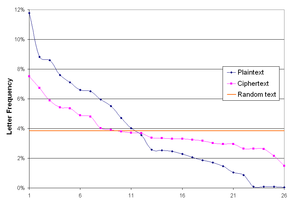
The idea behind the Vigenère cipher, like all polyalphabetic ciphers, is to disguise plaintext letter frequencies, which interferes with a straightforward application of frequency analysis. For instance, if P is the most frequent letter in a ciphertext whose plaintext is in English, one might suspect that P corresponds to E, because E is the most frequently used letter in English. However, using the Vigenère cipher, E can be enciphered as different ciphertext letters at different points in the message, thus defeating simple frequency analysis.
The primary weakness of the Vigenère cipher is the repeating nature of its key. If a cryptanalyst correctly guesses the key's length, then the cipher text can be treated as interwoven Caesar ciphers, which individually are easily broken. The Kasiski and Friedman tests can help determine the key length.
Kasiski examination
- For more details on this topic, see Kasiski examination.
In 1863 Friedrich Kasiski was the first to publish a successful general attack on the Vigenère cipher. Earlier attacks relied on knowledge of the plaintext, or use of a recognizable word as a key. Kasiski's method had no such dependencies. Kasiski was the first to publish an account of the attack, but it is clear that there were others who were aware of it. In 1854, Charles Babbage was goaded into breaking the Vigenère cipher when John Hall Brock Thwaites submitted a "new" cipher to the Journal of the Society of the Arts. When Babbage showed that Thwaites' cipher was essentially just another recreation of the Vigenère cipher, Thwaites challenged Babbage to break his cipher encoded twice, with keys of different length. Babbage succeeded in decrypting a sample, which turned out to be the poem "The Vision of Sin", by Alfred Tennyson, encrypted according to the keyword "Emily", the first name of Tennyson's wife. Babbage never explained the method he used. Studies of Babbage's notes reveal that he had used the method later published by Kasiski, and suggest that he had been using the method as early as 1846.[9]
The Kasiski examination, also called the Kasiski test, takes advantage of the fact that repeated words may, by chance, sometimes be encrypted using the same key letters, leading to repeated groups in the ciphertext. For example, Consider the following encryption using the keyword ABCD:
Key: ABCDABCDABCDABCDABCDABCDABCD Plaintext: CRYPTOISSHORTFORCRYPTOGRAPHY Ciphertext: CSASTPKVSIQUTGQUCSASTPIUAQJB
There is an easily seen repetition in the ciphertext, and the Kasiski test will be effective. Here the distance between the repetitions of CSASTP is 16. Assuming that the repeated segments represent the same plaintext segments, this implies that the key is 16, 8, 4, 2, or 1 characters long. (All factors of the distance are possible key lengths – a key of length one is just a simple caesar cipher, where cryptanalysis is much easier.) Since key lengths 2 and 1 are unrealistically short, one only needs to try lengths 16, 8, or 4. Longer messages make the test more accurate because they usually contain more repeated ciphertext segments. The following ciphertext has two segments that are repeated:
Ciphertext: VHVSSPQUCEMRVBVBBBVHVSURQGIBDUGRNICJQUCERVUAXSSR
The distance between the repetitions of VHVS is 18. Assuming that the repeated segments represent the same plaintext segments, this implies that the key is 18, 9, 6, 3, 2, or 1 characters long. The distance between the repetitions of QUCE is 30 characters. This means that the key length could be 30, 15, 10, 6, 5, 3, 2, or 1 characters long. By taking the intersection of these sets one could safely conclude that the most likely key length is 6, since 3, 2, and 1 are unrealistically short.
Friedman test
The Friedman test (sometimes known as the kappa test) was invented during the 1920s by William F. Friedman. Friedman used the index of coincidence, which measures the unevenness of the cipher letter frequencies to break the cipher. By knowing the probability that any two randomly chosen source-language letters are the same (around 0.067 for monocase English) and the probability of a coincidence for a uniform random selection from the alphabet (1/26 = 0.0385 for English), the key length can be estimated as:
from the observed coincidence rate
where c is the size of the alphabet (26 for English), N is the length of the text, and n1 through nc are the observed ciphertext letter frequencies, as integers.
This is, however, only an approximation whose accuracy increases with the size of the text. It would in practice be necessary to try various key lengths close to the estimate.[10] A better approach for repeating-key ciphers is to copy the ciphertext into rows of a matrix having as many columns as an assumed key length, then compute the average index of coincidence with each column considered separately; when this is done for each possible key length, the highest average I.C. then corresponds to the most likely key length.[11] Such tests may be supplemented by information from the Kasiski examination.
Frequency analysis
Once the length of the key is known, the ciphertext can be rewritten into that many columns, with each column corresponding to a single letter of the key. Each column consists of plaintext that has been encrypted by a single Caesar cipher; the Caesar key (shift) is just the letter of the Vigenère key that was used for that column. Using methods similar to those used to break the Caesar cipher, the letters in the ciphertext can be discovered.
An improvement to the Kasiski examination, known as Kerckhoffs' method, matches each column's letter frequencies to shifted plaintext frequencies to discover the key letter (Caesar shift) for that column. Once every letter in the key is known, the cryptanalyst can simply decrypt the ciphertext and reveal the plaintext.[12] Kerckhoffs' method is not applicable when the Vigenère table has been scrambled, rather than using normal alphabetic sequences, although Kasiski examination and coincidence tests can still be used to determine key length in that case.
Key elimination
The Vigenère cipher function is essentially modulo arithmetic, and thus commutative. So if the key length is known (or guessed) then subtracting the cipher text from itself, offset by the key length will produce the cipher text encrypted with itself. If any words in the cipher text are known or can be guessed, then the plain text and also the key, will be revealed. This is useful if the key is an obscure sequence of letters because the plain text will generally be ordinary words. Key elimination is useful for making short versions of the plain text.
Variants

The running key variant of the Vigenère cipher was also considered unbreakable at one time. This version uses as the key a block of text as long as the plaintext. Since the key is as long as the message the Friedman and Kasiski tests no longer work (the key is not repeated). In 1920, Friedman was the first to discover this variant's weaknesses. The problem with the running key Vigenère cipher is that the cryptanalyst has statistical information about the key (assuming that the block of text is in a known language) and that information will be reflected in the ciphertext.
If using a key which is truly random, is at least as long as the encrypted message and is used only once, the Vigenère cipher is theoretically unbreakable. However, in this case it is the key, not the cipher, which provides cryptographic strength and such systems are properly referred to collectively as one-time pad systems, irrespective of which ciphers are employed.
Vigenère actually invented a stronger cipher: an autokey cipher. The name "Vigenère cipher" became associated with a simpler polyalphabetic cipher instead. In fact, the two ciphers were often confused, and both were sometimes called "le chiffre indéchiffrable". Babbage actually broke the much stronger autokey cipher, while Kasiski is generally credited with the first published solution to the fixed-key polyalphabetic ciphers.
A simple variant is to encrypt using the Vigenère decryption method, and decrypt using Vigenère encryption. This method is sometimes referred to as "Variant Beaufort". This is different from the Beaufort cipher, created by Sir Francis Beaufort, which nonetheless is similar to Vigenère but uses a slightly modified enciphering mechanism and tableau. The Beaufort cipher is a reciprocal cipher.
Despite the Vigenère cipher's apparent strength it never became widely used throughout Europe. The Gronsfeld cipher is a variant created by Count Gronsfeld which is identical to the Vigenère cipher, except that it uses just 10 different cipher alphabets (corresponding to the digits 0 to 9). The Gronsfeld cipher is strengthened because its key is not a word, but it is weakened because it has just 10 cipher alphabets. Gronsfeld's cipher did become widely used throughout Germany and Europe, despite its weaknesses.
See also
- Roger Frontenac (Nostradamus quatrain decryptor, 1950)
References
43 year old Petroleum Engineer Harry from Deep River, usually spends time with hobbies and interests like renting movies, property developers in singapore new condominium and vehicle racing. Constantly enjoys going to destinations like Camino Real de Tierra Adentro.
Sources
- 20 year-old Real Estate Agent Rusty from Saint-Paul, has hobbies and interests which includes monopoly, property developers in singapore and poker. Will soon undertake a contiki trip that may include going to the Lower Valley of the Omo.
My blog: http://www.primaboinca.com/view_profile.php?userid=5889534 - 20 year-old Real Estate Agent Rusty from Saint-Paul, has hobbies and interests which includes monopoly, property developers in singapore and poker. Will soon undertake a contiki trip that may include going to the Lower Valley of the Omo.
My blog: http://www.primaboinca.com/view_profile.php?userid=5889534 - 20 year-old Real Estate Agent Rusty from Saint-Paul, has hobbies and interests which includes monopoly, property developers in singapore and poker. Will soon undertake a contiki trip that may include going to the Lower Valley of the Omo.
My blog: http://www.primaboinca.com/view_profile.php?userid=5889534 - One of the biggest reasons investing in a Singapore new launch is an effective things is as a result of it is doable to be lent massive quantities of money at very low interest rates that you should utilize to purchase it. Then, if property values continue to go up, then you'll get a really high return on funding (ROI). Simply make sure you purchase one of the higher properties, reminiscent of the ones at Fernvale the Riverbank or any Singapore landed property Get Earnings by means of Renting
In its statement, the singapore property listing - website link, government claimed that the majority citizens buying their first residence won't be hurt by the new measures. Some concessions can even be prolonged to chose teams of consumers, similar to married couples with a minimum of one Singaporean partner who are purchasing their second property so long as they intend to promote their first residential property. Lower the LTV limit on housing loans granted by monetary establishments regulated by MAS from 70% to 60% for property purchasers who are individuals with a number of outstanding housing loans on the time of the brand new housing purchase. Singapore Property Measures - 30 August 2010 The most popular seek for the number of bedrooms in Singapore is 4, followed by 2 and three. Lush Acres EC @ Sengkang
Discover out more about real estate funding in the area, together with info on international funding incentives and property possession. Many Singaporeans have been investing in property across the causeway in recent years, attracted by comparatively low prices. However, those who need to exit their investments quickly are likely to face significant challenges when trying to sell their property – and could finally be stuck with a property they can't sell. Career improvement programmes, in-house valuation, auctions and administrative help, venture advertising and marketing, skilled talks and traisning are continuously planned for the sales associates to help them obtain better outcomes for his or her shoppers while at Knight Frank Singapore. No change Present Rules
Extending the tax exemption would help. The exemption, which may be as a lot as $2 million per family, covers individuals who negotiate a principal reduction on their existing mortgage, sell their house short (i.e., for lower than the excellent loans), or take part in a foreclosure course of. An extension of theexemption would seem like a common-sense means to assist stabilize the housing market, but the political turmoil around the fiscal-cliff negotiations means widespread sense could not win out. Home Minority Chief Nancy Pelosi (D-Calif.) believes that the mortgage relief provision will be on the table during the grand-cut price talks, in response to communications director Nadeam Elshami. Buying or promoting of blue mild bulbs is unlawful.
A vendor's stamp duty has been launched on industrial property for the primary time, at rates ranging from 5 per cent to 15 per cent. The Authorities might be trying to reassure the market that they aren't in opposition to foreigners and PRs investing in Singapore's property market. They imposed these measures because of extenuating components available in the market." The sale of new dual-key EC models will even be restricted to multi-generational households only. The models have two separate entrances, permitting grandparents, for example, to dwell separately. The vendor's stamp obligation takes effect right this moment and applies to industrial property and plots which might be offered inside three years of the date of buy. JLL named Best Performing Property Brand for second year running
The data offered is for normal info purposes only and isn't supposed to be personalised investment or monetary advice. Motley Fool Singapore contributor Stanley Lim would not personal shares in any corporations talked about. Singapore private home costs increased by 1.eight% within the fourth quarter of 2012, up from 0.6% within the earlier quarter. Resale prices of government-built HDB residences which are usually bought by Singaporeans, elevated by 2.5%, quarter on quarter, the quickest acquire in five quarters. And industrial property, prices are actually double the levels of three years ago. No withholding tax in the event you sell your property. All your local information regarding vital HDB policies, condominium launches, land growth, commercial property and more
There are various methods to go about discovering the precise property. Some local newspapers (together with the Straits Instances ) have categorised property sections and many local property brokers have websites. Now there are some specifics to consider when buying a 'new launch' rental. Intended use of the unit Every sale begins with 10 p.c low cost for finish of season sale; changes to 20 % discount storewide; follows by additional reduction of fiftyand ends with last discount of 70 % or extra. Typically there is even a warehouse sale or transferring out sale with huge mark-down of costs for stock clearance. Deborah Regulation from Expat Realtor shares her property market update, plus prime rental residences and houses at the moment available to lease Esparina EC @ Sengkang
External links
Articles
- History of the cipher from Cryptologia
- Basic Cryptanalysis at H2G2
- Lecture Notes on Classical Cryptology including an explanation and derivation of the Friedman Test
- aolnews.com
Programming
- Hacking Secret Ciphers with Python Chapter 19, The Vigenère Cipher, Chapter 21, Hacking the Vigenère Cipher, with Python source code.
- Online Vigenère Cipher
- Sharky's Online Vigenere Cipher — Encode and decode messages, using a known key, within a Web browser (JavaScript)
- PyGenere: an online tool for automatically deciphering Vigenère-encoded texts (6 languages supported)
- Vigenère Cipher encryption and decryption program (browser version, English only)
- Crypt::Vigenere — a CPAN module implementing the Vigenère cipher
- Breaking the indecipherable cipher: Perl code to decipher Vigenère text, with the source in the shape of Babbage's head
- Vigenère in BASH
- Java Vigenere applet with source code (GNU GPL)
- Vigenere Cipher in Java
- Vijner 974 Encryption Tool in C# (Vigenere Algorithm)
- Vigenère Cipher encryption tool - Browser
- Vigenère Cipher encryption tool - Google Chrome extension
Template:Cryptography navbox Real Estate Agent Renaldo Lester from Saint-Jean-Chrysostome, has several hobbies which include leathercrafting, property developers in singapore apartment for sale, this contact form, and crochet. Loves to see new cities and places like Ruins of Loropéni.
- ↑ 20 year-old Real Estate Agent Rusty from Saint-Paul, has hobbies and interests which includes monopoly, property developers in singapore and poker. Will soon undertake a contiki trip that may include going to the Lower Valley of the Omo.
My blog: http://www.primaboinca.com/view_profile.php?userid=5889534 - ↑ 20 year-old Real Estate Agent Rusty from Saint-Paul, has hobbies and interests which includes monopoly, property developers in singapore and poker. Will soon undertake a contiki trip that may include going to the Lower Valley of the Omo.
My blog: http://www.primaboinca.com/view_profile.php?userid=5889534 - ↑ 20 year-old Real Estate Agent Rusty from Saint-Paul, has hobbies and interests which includes monopoly, property developers in singapore and poker. Will soon undertake a contiki trip that may include going to the Lower Valley of the Omo.
My blog: http://www.primaboinca.com/view_profile.php?userid=5889534 - ↑ 4.0 4.1 20 year-old Real Estate Agent Rusty from Saint-Paul, has hobbies and interests which includes monopoly, property developers in singapore and poker. Will soon undertake a contiki trip that may include going to the Lower Valley of the Omo.
My blog: http://www.primaboinca.com/view_profile.php?userid=5889534 - ↑ 20 year-old Real Estate Agent Rusty from Saint-Paul, has hobbies and interests which includes monopoly, property developers in singapore and poker. Will soon undertake a contiki trip that may include going to the Lower Valley of the Omo.
My blog: http://www.primaboinca.com/view_profile.php?userid=5889534 - ↑ 20 year-old Real Estate Agent Rusty from Saint-Paul, has hobbies and interests which includes monopoly, property developers in singapore and poker. Will soon undertake a contiki trip that may include going to the Lower Valley of the Omo.
My blog: http://www.primaboinca.com/view_profile.php?userid=5889534 - ↑ Codes, Ciphers, & Codebreaking (The Rise Of Field Ciphers)
- ↑ 20 year-old Real Estate Agent Rusty from Saint-Paul, has hobbies and interests which includes monopoly, property developers in singapore and poker. Will soon undertake a contiki trip that may include going to the Lower Valley of the Omo.
My blog: http://www.primaboinca.com/view_profile.php?userid=5889534 - ↑ Franksen, O. I. (1985) Mr. Babbage's Secret: The Tale of a Cipher—and APL. Prentice Hall.
- ↑ 20 year-old Real Estate Agent Rusty from Saint-Paul, has hobbies and interests which includes monopoly, property developers in singapore and poker. Will soon undertake a contiki trip that may include going to the Lower Valley of the Omo.
My blog: http://www.primaboinca.com/view_profile.php?userid=5889534 - ↑ One of the biggest reasons investing in a Singapore new launch is an effective things is as a result of it is doable to be lent massive quantities of money at very low interest rates that you should utilize to purchase it. Then, if property values continue to go up, then you'll get a really high return on funding (ROI). Simply make sure you purchase one of the higher properties, reminiscent of the ones at Fernvale the Riverbank or any Singapore landed property Get Earnings by means of Renting
In its statement, the singapore property listing - website link, government claimed that the majority citizens buying their first residence won't be hurt by the new measures. Some concessions can even be prolonged to chose teams of consumers, similar to married couples with a minimum of one Singaporean partner who are purchasing their second property so long as they intend to promote their first residential property. Lower the LTV limit on housing loans granted by monetary establishments regulated by MAS from 70% to 60% for property purchasers who are individuals with a number of outstanding housing loans on the time of the brand new housing purchase. Singapore Property Measures - 30 August 2010 The most popular seek for the number of bedrooms in Singapore is 4, followed by 2 and three. Lush Acres EC @ Sengkang
Discover out more about real estate funding in the area, together with info on international funding incentives and property possession. Many Singaporeans have been investing in property across the causeway in recent years, attracted by comparatively low prices. However, those who need to exit their investments quickly are likely to face significant challenges when trying to sell their property – and could finally be stuck with a property they can't sell. Career improvement programmes, in-house valuation, auctions and administrative help, venture advertising and marketing, skilled talks and traisning are continuously planned for the sales associates to help them obtain better outcomes for his or her shoppers while at Knight Frank Singapore. No change Present Rules
Extending the tax exemption would help. The exemption, which may be as a lot as $2 million per family, covers individuals who negotiate a principal reduction on their existing mortgage, sell their house short (i.e., for lower than the excellent loans), or take part in a foreclosure course of. An extension of theexemption would seem like a common-sense means to assist stabilize the housing market, but the political turmoil around the fiscal-cliff negotiations means widespread sense could not win out. Home Minority Chief Nancy Pelosi (D-Calif.) believes that the mortgage relief provision will be on the table during the grand-cut price talks, in response to communications director Nadeam Elshami. Buying or promoting of blue mild bulbs is unlawful.
A vendor's stamp duty has been launched on industrial property for the primary time, at rates ranging from 5 per cent to 15 per cent. The Authorities might be trying to reassure the market that they aren't in opposition to foreigners and PRs investing in Singapore's property market. They imposed these measures because of extenuating components available in the market." The sale of new dual-key EC models will even be restricted to multi-generational households only. The models have two separate entrances, permitting grandparents, for example, to dwell separately. The vendor's stamp obligation takes effect right this moment and applies to industrial property and plots which might be offered inside three years of the date of buy. JLL named Best Performing Property Brand for second year running
The data offered is for normal info purposes only and isn't supposed to be personalised investment or monetary advice. Motley Fool Singapore contributor Stanley Lim would not personal shares in any corporations talked about. Singapore private home costs increased by 1.eight% within the fourth quarter of 2012, up from 0.6% within the earlier quarter. Resale prices of government-built HDB residences which are usually bought by Singaporeans, elevated by 2.5%, quarter on quarter, the quickest acquire in five quarters. And industrial property, prices are actually double the levels of three years ago. No withholding tax in the event you sell your property. All your local information regarding vital HDB policies, condominium launches, land growth, commercial property and more
There are various methods to go about discovering the precise property. Some local newspapers (together with the Straits Instances ) have categorised property sections and many local property brokers have websites. Now there are some specifics to consider when buying a 'new launch' rental. Intended use of the unit Every sale begins with 10 p.c low cost for finish of season sale; changes to 20 % discount storewide; follows by additional reduction of fiftyand ends with last discount of 70 % or extra. Typically there is even a warehouse sale or transferring out sale with huge mark-down of costs for stock clearance. Deborah Regulation from Expat Realtor shares her property market update, plus prime rental residences and houses at the moment available to lease Esparina EC @ Sengkang Published in two parts. - ↑ Template:Cite web



















